Companies impacting national security laws, sanctions or export controls need comprehensive advice. We help clients safely navigate the full spectrum of government and compliance challenges, offering practical guidance and insights on navigating the national security landscape. We provide strategic advice, compliance counseling, transactional support, and leverage one of the industry’s deepest benches of regulatory defense and crisis management specialists.
DOJ Issues Notice of Proposed Rulemaking Restricting the Transfer of Certain Sensitive U.S.-Person Data
People
November 18, 2024 Download PDF
On October 21, 2024, the National Security Division (“NSD”) of the U.S. Department of Justice (“DOJ”) issued a notice of proposed rulemaking (“NPRM”) to regulate, restrict, and in some cases prohibit the sharing of certain U.S.-person data with “countries of concern,” — China, Cuba, Iran, North Korea, Russia, and Venezuela.[1] The NPRM expands upon and clarifies the advance notice of proposed rulemaking (“ANPRM”) that NSD issued in March. Once DOJ completes the rulemaking process, the final rule will create a significant new regulatory regime for data security that will affect the operations of many companies in the data-driven economy. If implemented, the rule will impact U.S. companies’ ability to pursue certain data sharing partnerships and arrangements with China and other countries of concern and will require companies to establish internal compliance programs to ensure conformity with DOJ and CISA security requirements.
Background
On February 28, 2024, President Biden issued an Executive Order on “Preventing Access to Americans’ Bulk Sensitive Data and United States Government-Related Data by Countries of Concern” (the “Order”) to address the national security threat identified by the Administration posed by foreign adversaries’ efforts to access and exploit the sensitive data of U.S. persons.[2] The Order instructed DOJ to issue regulations to advance the President’s central objective of “restrict[ing] access by countries of concern to Americans’ bulk sensitive personal data and United States Government-related data when such access would pose an unacceptable risk to the national security of the United States.”[3]
On March 5, 2024, DOJ published the ANPRM, which previewed DOJ’s proposed regulatory framework in line with the Order.[4] DOJ solicited comments on the ANPRM, and published the NPRM on October 21, 2024. DOJ requested additional public comments, which are due by November 28.
Implications
Broad Scope. DOJ’s proposed rule may broadly impact the types of data sharing partnerships and arrangements that U.S. companies are able to engage in with Chinese companies, and it is likely to implicate a large number of U.S. companies conducting business internationally. Restrictions on transactions involving vendor, employment, and non-passive investment agreements, together with their attendant reporting obligations, will require companies to carefully monitor their transactions to ensure compliance with DOJ and CISA security requirements. DOJ expects U.S. persons engaged in transactions within the rule’s scope to ensure that foreign counterparties are complying with the rule, and a U.S. person’s failure to conduct due diligence regarding its counterparties can constitute a violation of the rule.[5]
How to Prepare. After publication of the ANPRM, Assistant Attorney General for National Security Matthew Olsen provided four points of advice to companies: (1) know your data, (2) know where that data is going, (3) know who has access to the data, and (4) know your data sales.[6] Additionally, the NPRM may have second-order effects that businesses should consider. For instance, Chinese competitors looking to establish a footprint in U.S. markets may be limited to industries where data covered by the NPRM would be less prevalent. This could impact market dynamics in key industries including healthcare, defense, telecommunications, and other critical sectors.[7]
Companies will likely need to include specific contractual restrictions in agreements with foreign counterparties to ensure compliance with these new rules, and may need to consider adjusting diligence processes, contractual frameworks, and data oversight programs in order to fully comply with the rule, once finalized. DOJ will consider the strength of a given compliance program when determining whether to pursue an enforcement action or the magnitude of any enforcement action.
The NPRM
The NPRM proposes to prohibit or restrict U.S. persons from engaging in “covered transactions” with “covered persons” that involve “bulk sensitive personal data” or government-related data. The NPRM generally adopts the framework first proposed in the ANPRM, which we discuss below. The limited substantive changes clarify that U.S. subsidiaries of foreign entities qualify as “U.S. persons” for purposes of the NPRM, and add new categories of transactions that are exempt from the regulatory framework. Under the NPRM, DOJ also may provide case-by-case licenses to permit otherwise prohibited or restricted transactions, and DOJ may issue advisory opinions about the regulation. It would also require U.S. persons engaging in transactions subject to the rule to keep a full and accurate record of the transaction available for at least 10 years, and U.S. persons engaged in these transactions would be required to furnish such reports to DOJ upon request.[8] Finally, the NPRM also proposes penalties for violations.
1. “Countries of Concern” and “Covered Persons”
Countries of Concern. Who qualifies as a “covered person” (discussed below) primarily turns on which countries qualify as “countries of concern.” The NPRM identifies six countries of concern: China (including Hong Kong and Macau), Cuba, Iran, North Korea, Russia, and Venezuela. DOJ stated these designations are due to the “long-term pattern or serious instances of conduct significantly adverse to the national security of the United States or the security and safety of U.S. persons, and because they pose a significant risk of exploiting bulk sensitive personal data or government-related data.”[9] Data transactions with “countries of concern” or those identified as covered parties are prohibited if they do not qualify for an exemption or have an appropriate license.[10]
Covered Persons. The NPRM proposes four categories of “covered persons” who would be restricted from receiving access to U.S. persons’ data:
(a) Foreign entities that are 50 percent or more owned by a country of concern, organized under the laws of a country of concern, or have their principal place of business in a country of concern;
(b) Foreign entities that are 50 percent or more owned by a covered person;
(c) Foreign employees or contractors of countries of concern or entities that are covered persons; and
(d) Foreign individuals who are primarily resident in countries of concern.[11]
Additionally, the Attorney General can publicly designate a person or entity as a “covered person” under certain circumstances.[12] Under the NPRM’s terms, therefore, entities may qualify as “covered persons” without being physically located in the territory of a country of concern. For instance, certain foreign subsidiaries of a Chinese-domiciled business would be covered persons. Their employees, too, may qualify as covered persons.
“Covered persons” do not include “U.S. persons,”[13] who are defined broadly to include any U.S. citizen, national, or lawful permanent resident; any person in the United States; or any entity organized solely under the laws of the United States or any jurisdiction within the United States (including foreign branches).[14] The NPRM also clarifies an ambiguous aspect of the ANPRM, stating that U.S. subsidiaries of businesses domiciled in countries of concern are not themselves covered persons (although, as discussed below, the NPRM could still create complications for such a businesses in practice).
2. Prohibited and Restricted Data Categories
The NPRM regulates certain transactions that involve “sensitive personal data” that exceeds a “bulk” threshold. It also prohibits or restricts certain transactions that involve government-related data.
Sensitive Personal Data. The NPRM defines “sensitive personal data” as data that falls into these six categories:
(a) Two or more enumerated identifiers (defined as device-based identifiers like IMEIs, MAC addresses, or SIM card numbers, or social security numbers, driver’s licenses, or other government identification numbers) together, or a single enumerated identifier in “combination with other data that is disclosed by a transacting party pursuant to the transaction such that the listed identifier is linked or linkable to other listed identifiers or to other sensitive personal data”;
(b) Precise geolocation data (GPS coordinates);
(c) Biometric identifiers (facial images, voice prints and patterns, and retina scans);
(d) Human genomic data (DNA within each of the 24 distinct chromosomes in the cell nucleus, including results from genetic testing);
(e) Personal health data (height, weight, vital signs, symptoms, test results, diagnosis, and psychological diagnostics); and
(f) Personal financial data (information related to an individual’s credit, debit cards, bank accounts, and financial liabilities, including payment history).[15]
“Sensitive personal data” explicitly excludes public and nonpublic data that does not relate to an individual (e.g., trade secrets and proprietary information), data that is already legally public from government records or that is distributed widely via media, and personal communications.[16]
Bulk threshold. The NPRM’s prohibitions and restrictions on sensitive personal data apply only when data exceeds certain bulk thresholds. Here, “bulk” means any amount of covered data, regardless of whether such data is anonymized, pseudonymized, de-identified, or encrypted, that, in the aggregate, exceeds various specific thresholds over the 12 months before a covered data transaction:[17]
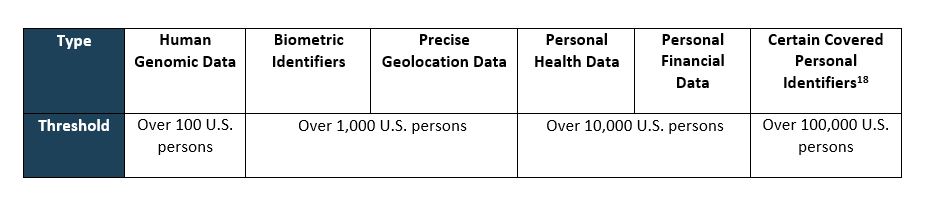 |
U.S. Government-Related Data. The NPRM also proposes to restrict or prohibit certain transactions with U.S. government-related data. Government-related data means: (1) data about the locations of government activities (i.e., any precise geolocation data that is within areas listed on DOJ’s Government-Related Location Data List),[19] and (2) data about U.S. government personnel (i.e., any sensitive personal data that is marketed as being linked to current or recently former U.S. government employees or contractors, including the U.S. military and intelligence community). As previewed in the ANPRM, the bulk thresholds do not apply to transactions involving government-related data. The proposed rule therefore applies to covered transactions of government-related data no matter the volume of data.[20]
3. Covered Data Transactions
The NPRM defines a “covered data transaction” as any transaction that involves government-related data or bulk U.S. sensitive data that involves a data brokerage, a vendor agreement, an employment agreement, or an investment agreement.[21] Under the NPRM, “covered data transactions” are either prohibited or restricted, except for certain exemptions. As compared to the ANPRM, the NPRM expands the definition of covered data transaction to “any transaction that involves any access to the data by the counterparty to a transaction,” rather than just transactions that involve government-related data or bulk U.S. sensitive personal data.[22]
Prohibited Transactions. The NPRM prohibits U.S. persons from knowingly engaging in a “covered data transaction” that involves either (1) data brokerage[23] with a country of concern or a covered person or (2) human genomic data or human biospecimens[24] over the bulk threshold with a country of concern or covered person. The prohibition attaches to any category of covered data transactions over the bulk threshold for transactions involving human genomic data or biospecimens.[25] This outright prohibition on this type of transaction, rather than a restriction, is designed to address risks posed by data transactions that would permit countries of concern to access U.S. persons’ human genomic data or provide countries of concern with human biospecimens. Thus, the NPRM prohibits U.S. persons from knowingly engaging in any covered data transaction that would provide a country of concern or covered person with access to bulk human genomic data or human biospecimens from which such data could be derived.
Restricted Transactions. The NPRM proposes to restrict (not prohibit) three categories of covered data transactions: vendor agreements,[26] employment agreements,[27] and non-passive investment agreements.[28] Entities may engage in these transactions only if they comply with applicable security requirements.
The security requirements, which have been promulgated by the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (“CISA”), mandate that U.S. persons engaging in restricted transactions must comply with certain organizational and system-level requirements (e.g., ensuring basic organizational cybersecurity policies, practices, and requirements are in place, in addition to other data-level requirements).[29] CISA’s security requirements are still subject to public comment and revision, and upon finalization, DOJ will incorporate by reference the final security requirements in the regime’s final rule. If transacting parties comply with these security (and other relevant) requirements, the NRPM provides that restricted transactions are not prohibited.
Exempt Transactions. The NPRM exempts nine classes of data transactions:[30]
- Personal communications;
- Information or informational materials as set out in 50 U.S.C. Sec. 1702(b)(3);
- Transactions incident to travel to or from a country;
- Official U.S. Government activities;
- Financial services, including investment management services, if the transactions are ancillary to those services;
- Corporate group transactions between U.S. entities and a foreign subsidiary or affiliate, so long as the transactions are part of ordinary business operations, (e.g., payroll, customer support, human resources, etc.);
- Transactions required or authorized by international agreements or federal law;
- Investment agreements, if CFIUS designates them as exempt or subjects the transactions to mitigation;
- Transactions necessary to provide telecommunications services, (e.g., data roaming and mobile voice calls);
- Drug, biological product, and medical device authorizations if transactions involve “regulatory approval data,” which is data that must be produced to a regulator before a business can research or market a drug, device, or other biological product; and
- Clinical investigations and post-marketing surveillance data for transactions regulated by the Food and Drug Administration (FDA) under the federal Food, Drug, and Cosmetic Act sections 505(i) and 520(g). Transactions may also be exempt if they are part of an FDA application seeking approval for research or marketing permits, or if the transactions involve providing the FDA with de-identified post-marketing surveillance data.
4. Licensing and Advisory Opinions
Licensing. The NPRM would authorize DOJ to grant licenses that authorize certain otherwise prohibited or restricted transactions. A party may also request approval for a specific transaction, if it discloses the details of the transaction in a license application to DOJ. The requirements and procedures for both general and specific licenses, including a process for reconsideration of denied information based on new information, are laid out in further detail in the NPRM.[31]
Guidance and Advisory Opinions. The NPRM would permit DOJ to issue general public guidance via agency responses to frequently asked questions, and it would authorize DOJ to issue advisory opinions addressing how the regulations would apply to specific proposed transactions.[32] Regulated parties can request advisory opinions on specific transactions, but parties will not be permitted to request advisory opinions on hypothetical scenarios.
5. Penalties and Reporting/Recordkeeping Requirements
Compliance Obligations. The NPRM contemplates compliance requirements for restricted transactions but does not set out general compliance requirements for all data transactions. Instead, those subject to the jurisdiction of the rules, if implemented, are expected to develop their own tailored compliance programs that take into account their “individualized risk profiles,” products and services, size, customer base, and geographic locations.[33] DOJ stated that, in the event of an enforcement action arising from a violation of the rules, it would consider the adequacy of the violator’s compliance program.[34]
As first explained in the ANPRM, the NPRM contemplates due diligence obligations for restricted transactions. These obligations will include required implementation of a comprehensive compliance program to verify and log items like data flows, sensitive data types and volume, and other information about the data. Furthermore, violators would be required to establish written policies on data security and compliance and certify them annually.[35]
Reporting Requirements. The NPRM did not alter the reporting requirements previewed in the ANPRM. Reporting is triggered when: (1) U.S. persons engage in restricted transactions and they are at least 25% owned by a country of concern or covered person; (2) a U.S. person receives and affirmatively rejects an offer to engage in a prohibited transaction; (3) a U.S. person that is engaged in a covered data transaction knows or suspects that a foreign counterparty is violating restrictions under the NPRM; and (4) a U.S. person invokes the exemption for certain data transactions available for drug, biological product, and medical device authorizations, and they seek regulatory approval to market that drug, biological product, or medical device in a country of concern.[36]
Enforcement. The NPRM grants DOJ broad authority to enforce its regulatory regime, including through conducting investigations, holding hearings, examining and deposing witnesses, and issuing subpoenas related to any matter being investigated.[37] Violators would face civil penalties of $368,136 per violation or twice the amount of the transaction involved, whichever amount is greater.[38] Willful violators would be subject to fines up to $1 million and up to 20 years in prison.[39] The NPRM furthermore sets out a procedure through which parties can respond before DOJ issues a penalty.[40]
* * *
[1] NPRM on Provisions Pertaining to Preventing Access to U.S. Sensitive Personal Data and Government-Related Data by Countries of Concern or Covered Persons, C.F.R. Part 202, Docket No. NSD 104, available here; see also Paul Weiss, Invoking National Security Risks, President Biden Issues Executive Order Restricting the Transfer of Certain Sensitive U.S. Personal Data to Countries of Concern (Feb. 29, 2024), available here.
[2] The White House, Executive Order 14117 on Preventing Access to Americans’ Bulk Sensitive Personal Data and United States Government-Related Data by Countries of Concern (Feb. 28, 2024), available here.; see also Paul, Weiss, Invoking National Security Risks, President Biden Issues Executive Order Restricting the Transfer of Certain Sensitive U.S. Personal Data to Countries of Concern (Feb. 29, 2024), available here.
[3] Id.
[4] ANPRM on Provisions Regarding Access to Americans' Bulk Sensitive Personal Data and Government-Related Data by Countries of Concern, 28 C.F.R. Part 202, Docket No. NSD 104, available here.
[5] NPRM at 57-58.
[6] Dep’t of Justice, Assistant Attorney General Matthew G. Olsen Delivers Keynote Speech at the American Bar Association’s 39th National Institute on White Collar Crime (Mar. 8, 2024), available here.
[7] See generally, John Carlin et al., Bulk Sensitive Data Transfer Rule Would Tighten Security Controls, Bloomberg (Mar. 19, 2024), available here.
[8] NPRM at 408-413, §§ 202.1101, 202.1102.
[9] NPRM at 99-127, 393-394; § 202.601.
[10] NPRM at 362-365, 372-373; §§ 202.301-302, 202.401.
[11] NPRM at 330-331, § 202.211.
[12] NPRM at 394-395, § 202.701.
[13] NPRM at 340, § 202.221 (“The term foreign person means any person that is not a U.S. person.”).
[14] NPRM at 359; § 202.256; see also id. at 359-360 (providing examples of U.S. persons).
[15] NPRM at 356-357; § 202.249.
[16] NPRM at 356-357; § 202.249.
[17] NPRM at 326-28; §§ 202.205, 202.206.
[18] NPRM at 237; § 202.205 (“(f) Covered personal identifiers collected about or maintained on more than 100,000 U.S. persons; or (g) Combined data, meaning any collection or set of data that contains more than one of the categories in paragraphs (a) through (g) of this section, or that contains any listed identifier linked to categories in paragraphs (a) through (e) of this section, where any individual data type meets the threshold number of persons or devices collected or maintained in the aggregate for the lowest number of U.S. persons or U.S. devices in that category of data.”)
[19] NPRM at 340-341, 421-422; §§ 202.222, 202.1401.
[20] NPRM at 340-341; § 202.222.
[21] NPRM at 329; § 202.210.
[22] Id.
[23] “’Data brokerage’ means the sale of data, licensing of access to data, or similar commercial transactions involving the transfer of data from any person (the provider) to any other person (the recipient), where the recipient did not collect or process the data directly from the individuals linked or linkable to the collected or processed data.” See NPRM at 335; § 202.214.
[24] “’Human genomic data’ means data representing the nucleic acid sequences that constitute the entire set or a subset of the genetic instructions found in a human cell, including the result or results of an individual’s ‘genetic test’ (as defined in 42 U.S.C. 300gg-91(d)(17)) and any related human genetic sequencing data.” See NPRM at 342; § 202.224.
[25] NPRM at 366, § 202.303.
[26] Vendor Agreements are defined as “[a]ny agreement or arrangement, other than an employment agreement, in which any person provides goods or services to another person, including cloud-computing services, in exchange for payment or other consideration.” NPRM at 360; § 202.258.
[27] Employment Agreements are defined as “[a]ny agreement or arrangement in which an individual, other than as an independent contractor, performs work or performs job functions directly for a person in exchange for payment or other consideration, including employment on a board or committee, executive-level arrangements or services, and employment services at an operational level.” NPRM at 337-338; § 202.217.
[28] A non-passive Investment Agreement would be an investment agreement that provides a foreign technology company with enough of an ownership interest that it can become involved in substantive business and strategy decisions. Such agreements would provide the foreign technology company with the ability to obtain access to data, even if the investment agreement is silent on the issue or even in situations where the agreement explicitly forbids that access. Where the investment agreement would involve the ability to access bulk U.S. sensitive personal data, it is a restricted transaction. NPRM at 346; § 202.228 Example 3.
[29] See CISA, Proposed Security Requirements For Restricted Transactions (Oct. 2024), available here.
[30] NPRM at 375-393; §§ 202.501-202.511.
[31] NPRM at 397-402; §§ 202.801-202.803.
[32] NPRM at 402-405 ; § 202.901.
[33] See Dep’t of Justice, FACT SHEET: Justice Department Moving Forward with Publishing a Proposed Rule to Protect Americans’ Sensitive Personal Data from Countries of Concern at 6. (Oct. 21, 2024), available here.
[34] NPRM at 144.
[35] NPRM at 405-406; § 202.1001.
[36] NPRM at 410-414; §§ 202.1102-202.1104.
[37] NPRM at 410; § 202.1102.
[38] NPRM at 416; § 202.1301. Civil penalties are subject to the Federal Civil Penalties Inflation Adjustment Act of 1990 (Public Law 101-410, as amended, 28 U.S.C. § 2461).
[39] NPRM at 416; § 202.1301.
[40] NPRM at 421; § 202.1306.



